Azure AD B2C App registration
Azure Active Directory B2C provides business-to-customer identity as a service. It allows users to use their preferred social, enterprise, or local account identities to get single sign-on access to your applications and APIs.
This post provides some information on creating app registration, set up endpoints , acquire token etc..
First lets create a App registration in Azure AD B2C like below.
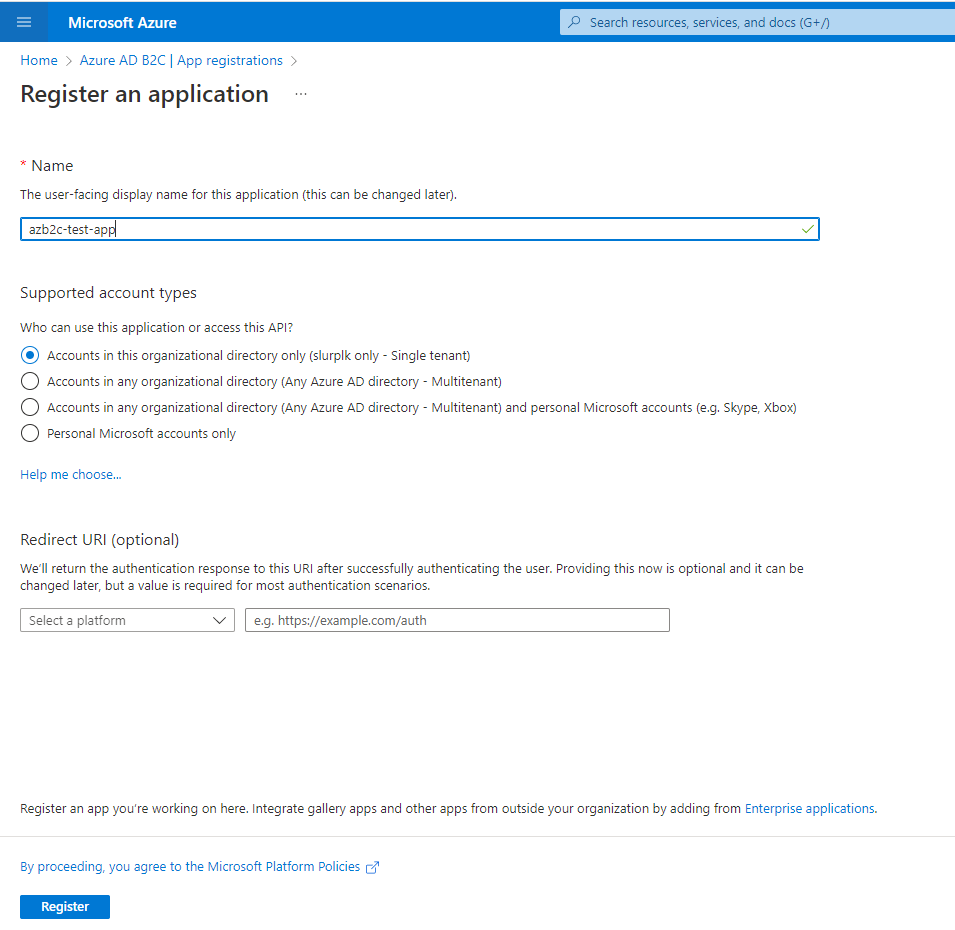
Then add a new client secret and copy the value of it.
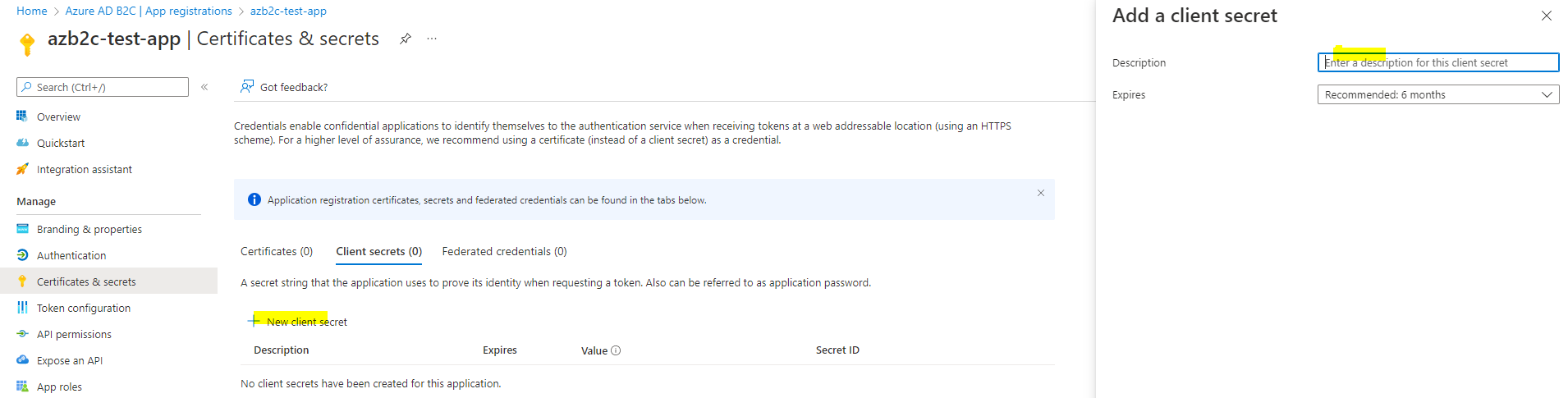
Also change the app manifest and update the accessTokenAcceptedVersion attribute to 2 as below.
Now we can use those details to acquire a token using client credential flow. Lets look at how we can do this using postman.
To do this first you need to collect below details from your Azure B2C app registration we created above.
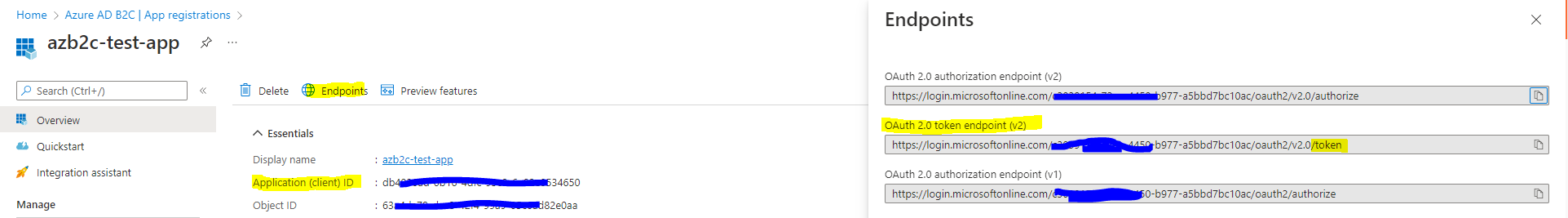
Collect the client id , OAuth 2.0 token endpoint (v2) as above screen. you also need the client secret created above for this.
Now in postman give the details as below. for the scope we'll use .default.
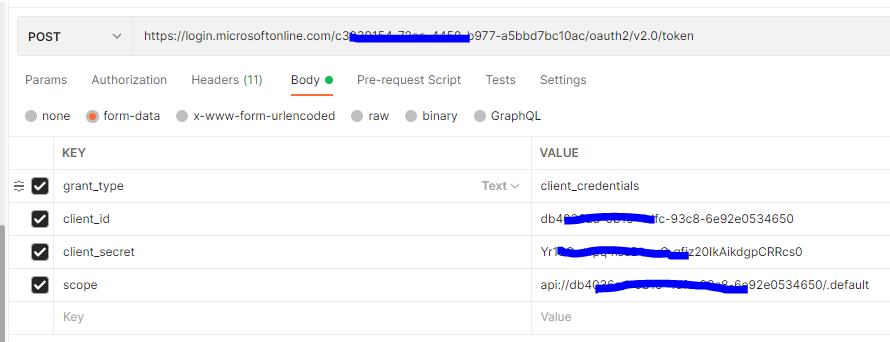
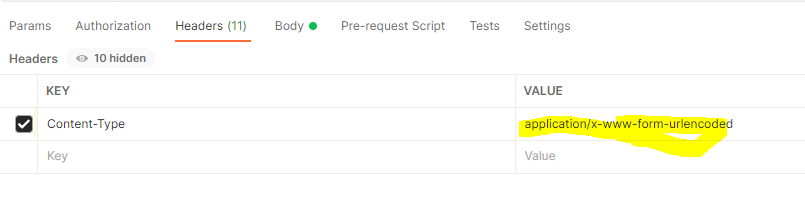
Also make sure you add the Content-Type header with value application/x-www-form-urlencoded.
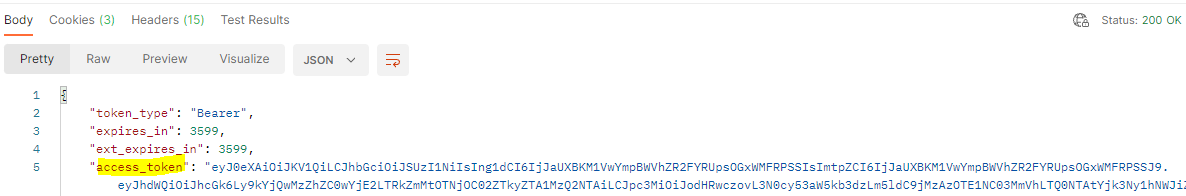
That's All! Now you will be able to get the access_token like below.
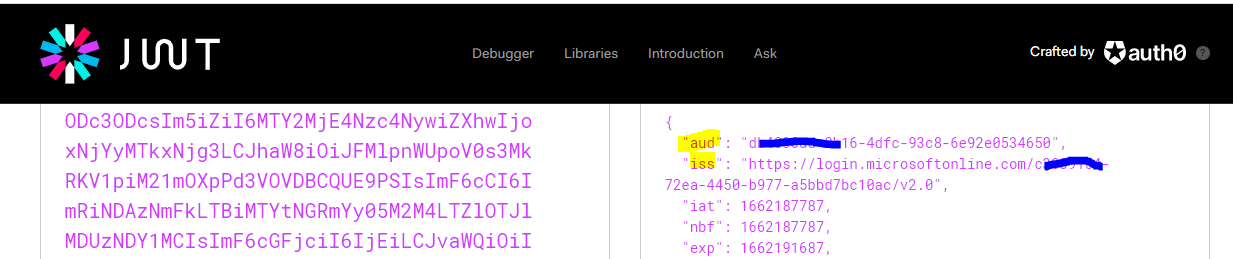
You can use https://jwt.io/ to decode and check the access_token.
Application permissions
So far we looked at how we can create an app registration and use it for OAuth 2.0 client credentials flow. This type of grant is commonly used for server-to-server (often referred to as daemon application) interactions that runs in the background, without immediate interaction with a user.
Now lets look at how we can extend this to use application permissions (app roles). To use app roles, we need two things:
- An API which is secured by Azure AD B2C and provide access to endpoint only for the requests with access tokens added in the authorization header.
- A client application which will obtain an access token from the Azure AD B2C using client credentials flow and use it with requests to the above secured API.
First let's extend the same app registration we created above and expose two app roles. To do that I'll use the Manifest file (instead of using the UI).
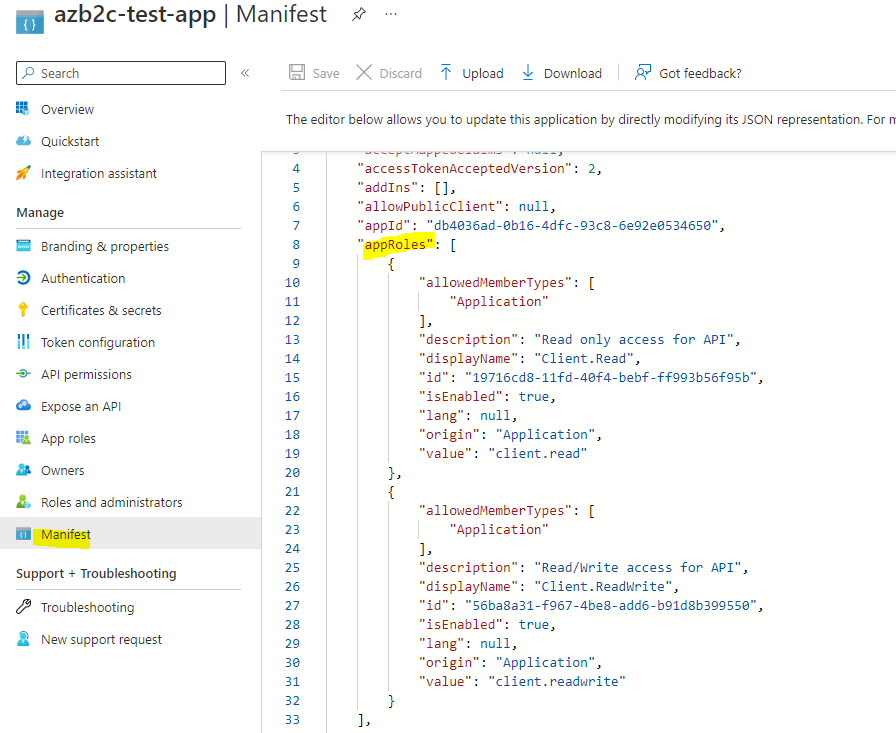
To modify the manifest, select Manifest section and update appRoles property which is empty by default with below value.
{
"allowedMemberTypes": [
"Application"
],
"description": "Read only access for API",
"displayName": "Client.Read",
"id": "19716cd8-11fd-40f4-bebf-ff993b56f95b",
"isEnabled": true,
"lang": null,
"origin": "Application",
"value": "client.read"
},
{
"allowedMemberTypes": [
"Application"
],
"description": "Read/Write access for API",
"displayName": "Client.ReadWrite",
"id": "56ba8a31-f967-4be8-add6-b91d8b399550",
"isEnabled": true,
"lang": null,
"origin": "Application",
"value": "client.readwrite"
}It should look like below after update. Note that you can use any unique Guid for roles.
Then let's move on to create app registration for client application. First I created an app registration and added a new client secret. ( same as what we did in beginning of this post).
Then move on to the API Permissions Tab and click "Add a permission" and find your "App registration for API" under the My APIs Tab. (This is the App registration you created for representing your API with two added read and write roles in Manifest file). You can select which permissions you wanted to grant for the client application like below.
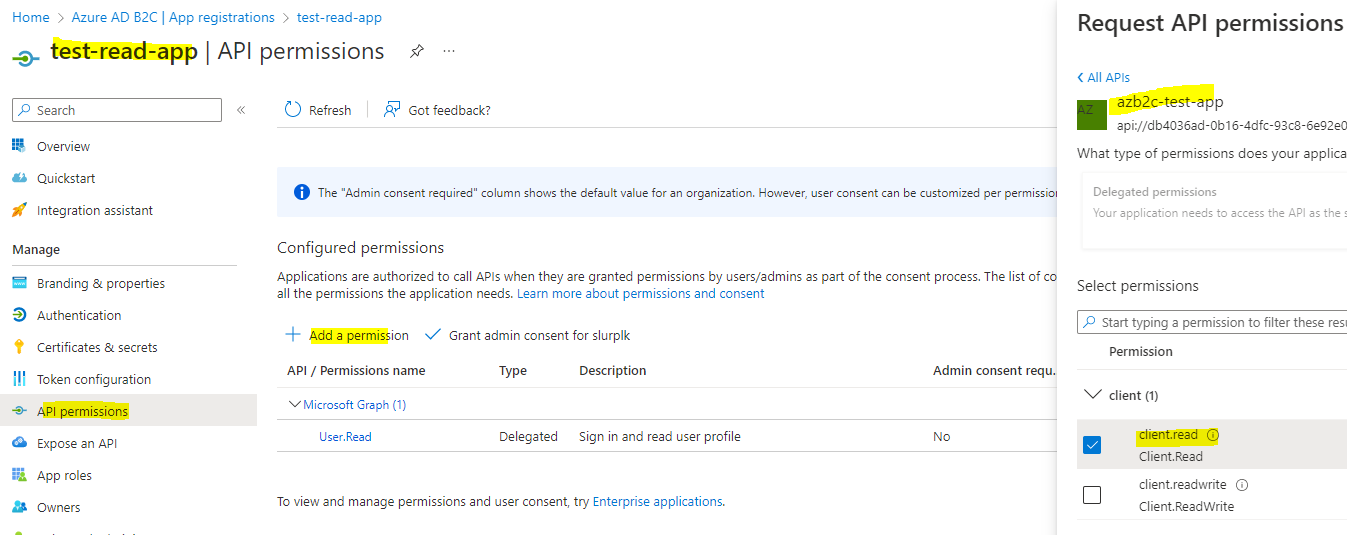
Also note that you need to grant admin consent by clicking the "Grant admin consent for xxxxx".
Finally for testing this, we can use the postman and same steps we did earlier. The only difference is that we use the details of newly created client app registration( client_id and client_secret ).
You if I use https://jwt.io/ to decode and check the access_token, now you would be able to see the roles like below.
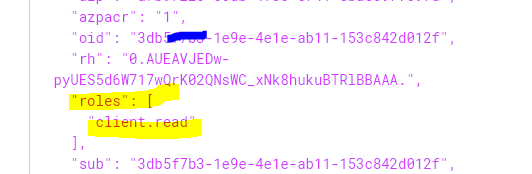
With this setup, client (deamon application) can request an access_token using OAuth 2.0 client credentials flow( using client_id and client_secret) and pass it to the secured API which in turn will validate the token and app roles as a part of authorizing the request.
